Permission Manager
Permission Manager是一个为Kubernetes RBAC和用户管理提供Web UI的项目,为Kubernetes权限管理提供友好的可视化界面。
安装
从 https://github.com/sighupio/permission-manager/tree/master/deployments/kubernetes 把yaml文件下载下来,如下
- [root@qd01-stop-k8s-master001kubernetes]#ll
- total4
- -rw-r–r–1rootroot2697Jan2811:08deploy.yml
- drwxr-xr-x2rootroot37Jan2811:14seeds
创建namespace
- [root@qd01-stop-k8s-master001kubernetes]#kubectlcreatenamespacepermission-manager
- namespace/permission-managercreated
创建秘密并进行相应更新
- [rancher@qd01-stop-k8snode011permission-manager]$catsecret.yaml
- —
- apiVersion:v1
- kind:Secret
- metadata:
- name:permission-manager
- namespace:permission-manager
- type:Opaque
- stringData:
- PORT:"4000"#portwhereserverisexposed
- CLUSTER_NAME:"kubernetes-cluster"#nameoftheclustertouseinthegeneratedkubeconfigfile
- CONTROL_PLANE_ADDRESS:"https://10.26.29.208:6443"#fulladdressofthecontrolplanetouseinthegeneratedkubeconfigfile
- BASIC_AUTH_PASSWORD:"Admin"#passwordusedbybasicauth(usernameis`admin`)
- [root@qd01-stop-k8s-master001kubernetes]#kubectlapply-fsecret.yaml
- secret/permission-managercreated
部署
- [root@qd01-stop-k8s-master001seeds]#kubectlapply-fcrd.yml
- Warning:apiextensions.k8s.io/v1beta1CustomResourceDefinitionisdeprecatedinv1.16+,unavailableinv1.22+;useapiextensions.k8s.io/v1CustomResourceDefinition
- customresourcedefinition.apiextensions.k8s.io/permissionmanagerusers.permissionmanager.usercreated
- [root@qd01-stop-k8s-master001seeds]#kubectlapply-fseed.yml
- clusterrole.rbac.authorization.k8s.io/template-namespaced-resources___operationcreated
- clusterrole.rbac.authorization.k8s.io/template-namespaced-resources___developercreated
- clusterrole.rbac.authorization.k8s.io/template-cluster-resources___read-onlycreated
- clusterrole.rbac.authorization.k8s.io/template-cluster-resources___admincreated
- [root@qd01-stop-k8s-master001kubernetes]#kubectlapply-fdeploy.yml
- service/permission-managercreated
- deployment.apps/permission-managercreated
- serviceaccount/permission-managercreated
- clusterrole.rbac.authorization.k8s.io/permission-managercreated
- Warning:rbac.authorization.k8s.io/v1beta1ClusterRoleBindingisdeprecatedinv1.17+,unavailableinv1.22+;userbac.authorization.k8s.io/v1ClusterRoleBinding
- clusterrolebinding.rbac.authorization.k8s.io/permission-managercreated
以上就把permission-manager部署好了,Warning信息可忽略或者自行修改yaml文件中api版本为rbac.authorization.k8s.io/v1
使用ingress暴露服务
创建ingress.yaml
- apiVersion:networking.k8s.io/v1
- kind:Ingress
- metadata:
- name:permission-manager-ingress
- namespace:permission-manager
- annotations:
- kubernetes.io/ingress.class:nginx
- spec:
- rules:
- -host:permission.kubeops.net
- http:
- paths:
- -pathType:Prefix
- path:/
- backend:
- service:
- name:permission-manager
- port:
- number:4000
- [root@qd01-stop-k8s-master001kubernetes]#kubectlapply-fingress.yaml
- [root@qd01-stop-k8s-master001kubernetes]#kubectlgeting-npermission-manager
- Warning:extensions/v1beta1Ingressisdeprecatedinv1.14+,unavailableinv1.22+;usenetworking.k8s.io/v1Ingress
- NAMECLASSHOSTSADDRESSPORTSAGE
- permission-manager-ingress<none>permission.kubeops.net10.26.29.202,10.26.29.203804m8s
自行添加dns解析,然后浏览器访问permission.kubeops.net,使用用户名密码(在secret中设置的)登录
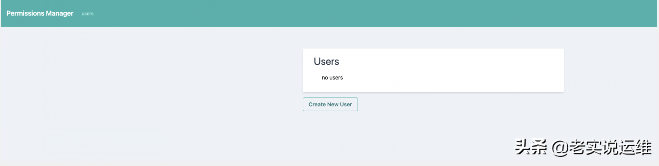
登录
目前没有任何的用户,我们可以创建一个普通用户测试下
创建用户
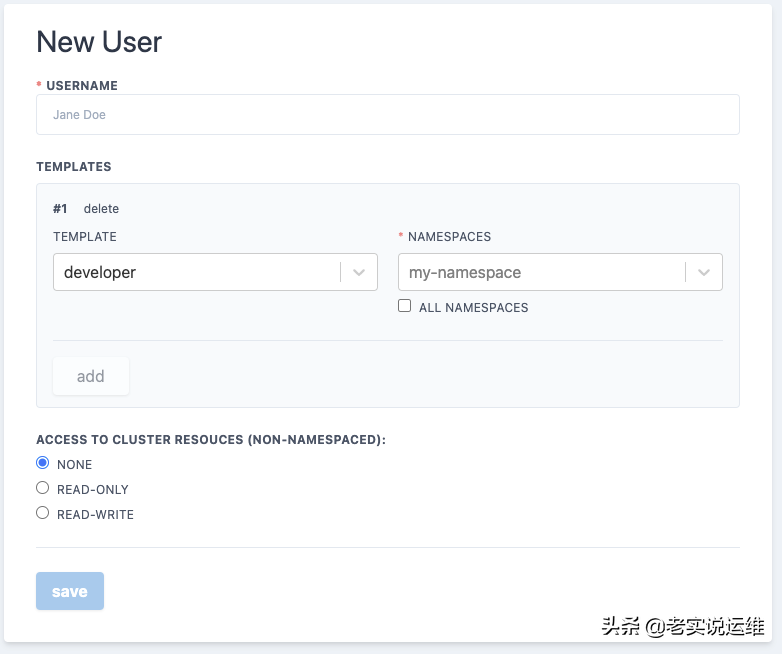
点击Create New User
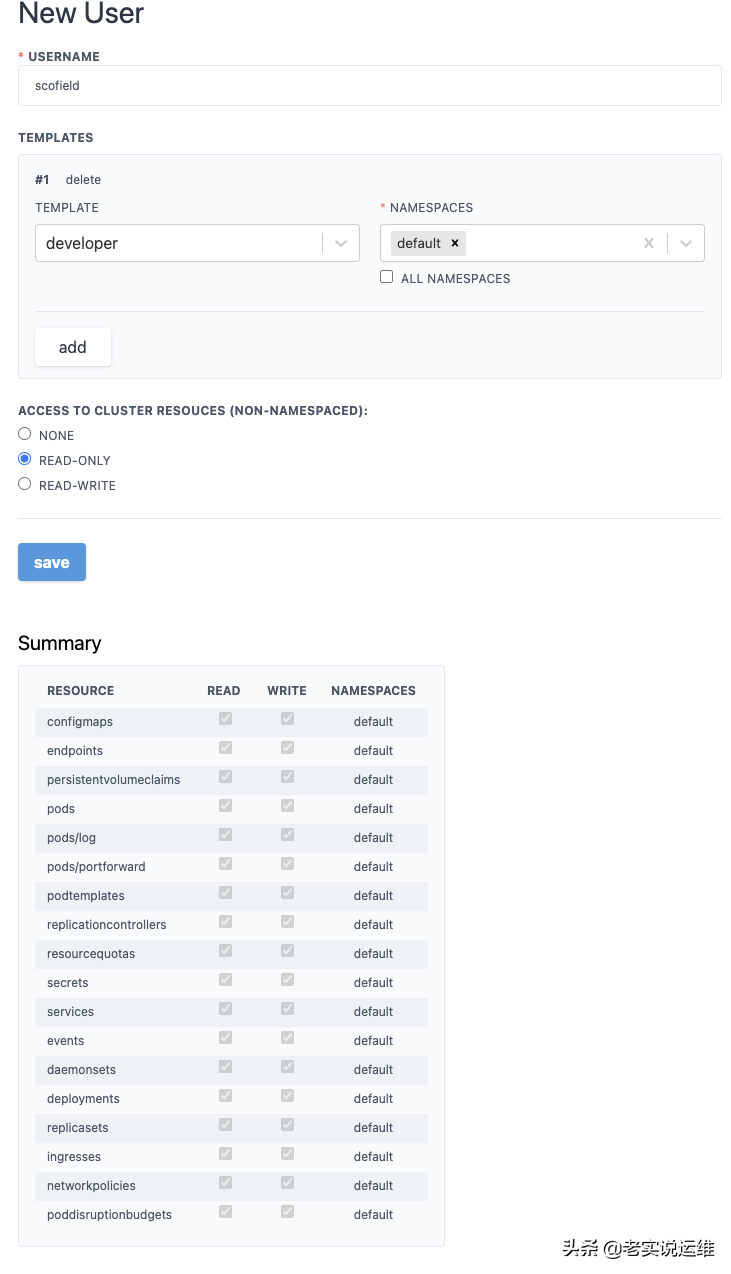
填写相关信息
然后点击Save即可
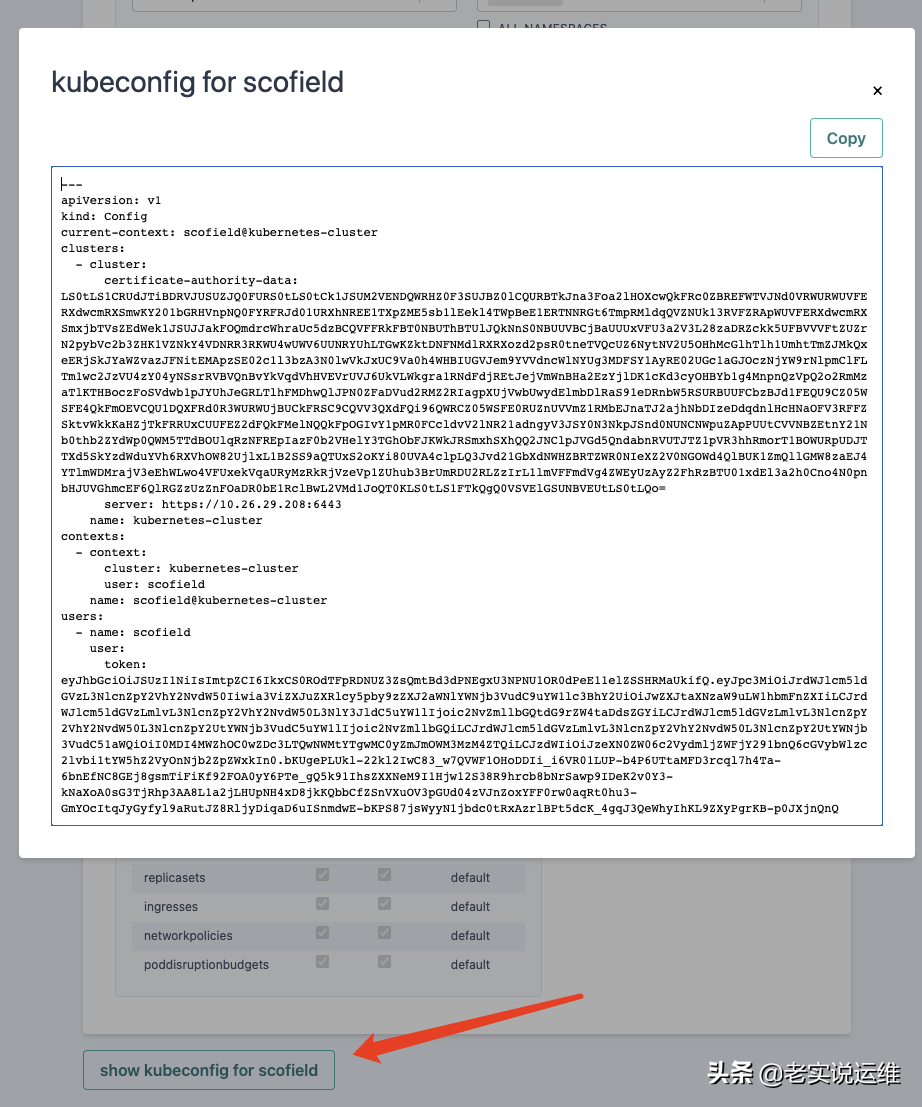
在用户信息下可以查看生成的config文件
测试
保存config文件,然后使用这个配置文件访问集群
我这里把config文件拷贝到本地,重命名为scofield,使用kubectl测试
- [root@qd01-stop-k8s-master001kubernetes]#kubectl–kubeconfig=scofieldgetpo
- Noresourcesfoundindefaultnamespace.
- [root@qd01-stop-k8s-master001kubernetes]#kubectl–kubeconfig=scofieldgetpo-nargo
- Errorfromserver(Forbidden):podsisforbidden:User"system:serviceaccount:permission-manager:scofield"cannotlistresource"pods"inAPIgroup""inthenamespace"argo"
从以上输出可以看出,我分别查询的两个namespace,分别是default和argo,但是只有default这个命名空间有权限,而argo这个命名空间是没有权限操作的。这跟我们在创建用户是赋予的权限是一致的。
更多信息请查看官网
原文地址:https://www.toutiao.com/i6922693218366685699/